Defend Tirelessly!
Partner with us to transform your cybersecurity into a strategic advantage. From safeguarding critical assets and sensitive data to defeating malware and securing digital infrastructure, we provide the expertise and innovation needed to reduce risk and streamline your security operations. Let’s build a safer future—starting today.
At Halcyon Cyberworks, we know cybersecurity isn’t just a necessity—it’s the foundation of your success. Let us help you turn cybersecurity into your competitive edge! force multiplier! strategic advantage!
Cloud-native Security Operations
Secure your business with strategies built for today’s cloud-first operations.
AI-Enhanced Threat Detection
Leverage AI to identify and neutralize cyber risks before they escalate.
Next-Generation Security Tools
Be more secure with forward-looking tools designed for dynamic environments.
Dynamic & Scalable Solutions
Flexible security strategies that grow with your business, countering new threats.
No-code / Low-code Automation
Automate security workflows effortlessly for streamlined operations.
24x7x365 SOC-enabled Defense
From endpoint to the cloud; and every digital space in between.
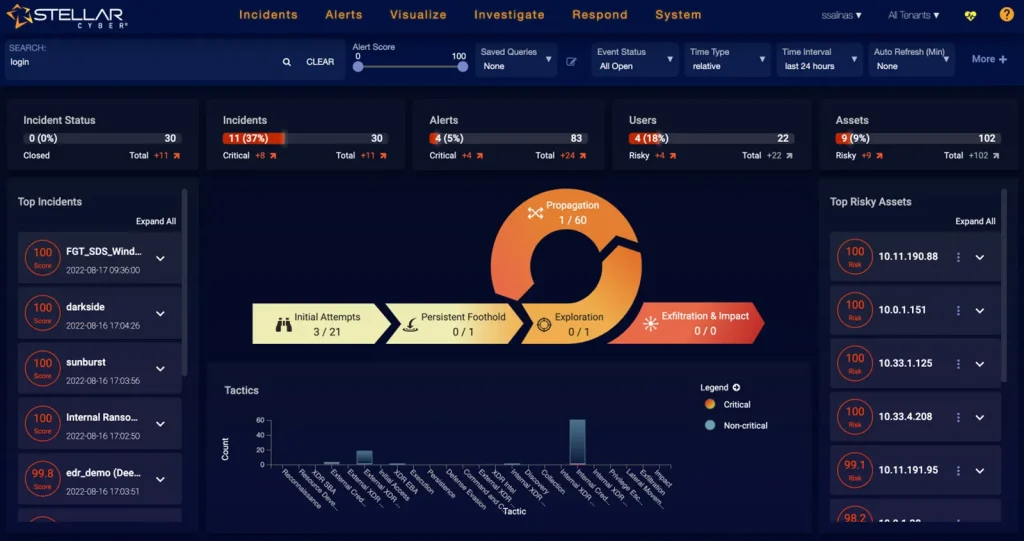

Strategy
Strategy
A sound cyberdefense strategy is your organization’s blueprint for staying secure in an ever-evolving threat landscape. Our tailored approach combines cutting-edge technology, proactive monitoring, and rapid response to safeguard your critical assets and ensure business continuity.
Discover more
XDR - eXtended Detection & Response
eXtended Detection & Response
XDR simplifies threat detection, analysis, and response by unifying data across your network, endpoints, and cloud environments. With enhanced visibility and automated responses, it ensures comprehensive security to keep your business protected.
Discover more
NDR - Network Detection & Response
Network Detection & Response
NDR delivers advanced threat detection and response by analyzing network traffic for malicious activity. With real-time visibility and proactive threat hunting, it ensures your network remains secure against evolving cyber threats.
Discover more
RMM - Remote Monitoring & Management
Remote Monitoring & Management
Gain complete control over your IT infrastructure with proactive tools that monitor and manage systems remotely. RMM streamlines operations, resolves issues faster, and ensures optimal performance across your network and devices.
Discover more
UEBA - User & Entity Behavior Analytics
User & Entity Behavior Analytics
Detect anomalies and prevent threats by analyzing patterns in user and entity behavior. UEBA provides deep insights into unusual activities, helping to identify risks and strengthen your security posture.
Discover more
CSPM - Cloud Sec Posture Management
Cloud Security Posture Management
Ensure your cloud environments are secure and compliant with tools that monitor configurations and identify vulnerabilities. CSPM helps prevent misconfigurations, enforce policies, and protect against potential threats in the cloud.
Discover more
ASM - Attack Surface Management
Attack Surface Management
Proactively identify and reduce your exposure to threats by continuously monitoring your digital assets. ASM provides visibility into potential vulnerabilities, helping to secure your organization against evolving cyber risks.
Discover more
SIEM - Sec Info and Event Management
Security Information and Event Management
Harness the power of centralized data collection and analysis to detect and respond to threats faster. SIEM integrates logs and events from across your systems, delivering actionable insights to strengthen your security.
Discover more
SOAR -Sec Orch, Auto, & Response
Sec Orchestration, Automation, & Response
Automate and streamline your security operations with tools that orchestrate responses to threats. SOAR enhances efficiency, reduces response times, and empowers your team to focus on critical priorities.
Discover more
AI-Native Workflow Automation
AI-Native Workflow Automation
Revolutionize your security operations with intelligent automation that adapts and evolves. AI-native workflow tools simplify complex processes, enhance efficiency, and strengthen your defense against emerging threats.
Discover more
-
Strategy
-
XDR - eXtended Detection & Response
-
NDR - Network Detection & Response
-
RMM - Remote Monitoring & Management
-
UEBA - User & Entity Behavior Analytics
-
CSPM - Cloud Sec Posture Management
-
ASM - Attack Surface Management
-
SIEM - Sec Info and Event Management
-
SOAR -Sec Orch, Auto, & Response
-
AI-Native Workflow Automation
Strategy
A sound cyberdefense strategy is your organization’s blueprint for staying secure in an ever-evolving threat landscape. Our tailored approach combines cutting-edge technology, proactive monitoring, and rapid response to safeguard your critical assets and ensure business continuity.
Discover more
eXtended Detection & Response
XDR simplifies threat detection, analysis, and response by unifying data across your network, endpoints, and cloud environments. With enhanced visibility and automated responses, it ensures comprehensive security to keep your business protected.
Discover more
Network Detection & Response
NDR delivers advanced threat detection and response by analyzing network traffic for malicious activity. With real-time visibility and proactive threat hunting, it ensures your network remains secure against evolving cyber threats.
Discover more
Remote Monitoring & Management
Gain complete control over your IT infrastructure with proactive tools that monitor and manage systems remotely. RMM streamlines operations, resolves issues faster, and ensures optimal performance across your network and devices.
Discover more
User & Entity Behavior Analytics
Detect anomalies and prevent threats by analyzing patterns in user and entity behavior. UEBA provides deep insights into unusual activities, helping to identify risks and strengthen your security posture.
Discover more
Cloud Security Posture Management
Ensure your cloud environments are secure and compliant with tools that monitor configurations and identify vulnerabilities. CSPM helps prevent misconfigurations, enforce policies, and protect against potential threats in the cloud.
Discover more
Attack Surface Management
Proactively identify and reduce your exposure to threats by continuously monitoring your digital assets. ASM provides visibility into potential vulnerabilities, helping to secure your organization against evolving cyber risks.
Discover more
Security Information and Event Management
Harness the power of centralized data collection and analysis to detect and respond to threats faster. SIEM integrates logs and events from across your systems, delivering actionable insights to strengthen your security.
Discover more
Sec Orchestration, Automation, & Response
Automate and streamline your security operations with tools that orchestrate responses to threats. SOAR enhances efficiency, reduces response times, and empowers your team to focus on critical priorities.
Discover more
AI-Native Workflow Automation
Revolutionize your security operations with intelligent automation that adapts and evolves. AI-native workflow tools simplify complex processes, enhance efficiency, and strengthen your defense against emerging threats.
Discover more
Cybersecurity leaders have spoken...
Cybersecurity complexity and workload have increased
My organization's cybersecurity team is understaffed
Regulatory compliance has become more difficult.
...rating the current state of their org's CySec culture...
ADVANCED:
31%
Cybersecurity is considered a shared responsibility by ALL employees and is included in all business/mission initiatives
AVERAGE:
43%
Cybersecurity is considered a shared responsibility by SOME employees and is included in all business/mission initiatives
FAIR:
20%
While my organization makes some efforts, cybersecurity is only partially considered a shared responsibility by employees and partially included in business/ mission initiatives
POOR:
7%
My organization makes little cybersecurity efforts, so cybersecurity is hardly considered a shared responsibility by employees and hardly included in business/mission initiatives
...and the impact of the cybersecurity skills shortage...
Degree of Difficulty Recruiting and Hiring Cybersecurity Staff
Within the overall survey population, a majority (88%) of respondents say it is extremely difficult, difficult, or somewhat difficult to recruit and hire cybersecurity professionals, representing a 12% increase over 2021.
Add Your Heading Text Here
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Degree of Difficulty Recruiting and Hiring Cybersecurity Staff
Within the overall survey population, a majority (88%) of respondents say it is extremely difficult, difficult, or somewhat difficult to recruit and hire cybersecurity professionals, representing a 12% increase over 2021.
Example Title
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Mauris tempus nisl vitae magna pulvinar laoreet. Nullam erat ipsum, magna pulvinar laoreet. Nullam erat ipsum,magna pulvinar laoreet. Nullam erat ipsum,
...and Halcyon Cyberworks has the answer!
Why choose Halcyon?
Why choose Us?
Our managed cybersecurity services provide proactive protection, 24/7 monitoring, and expert threat response to safeguard your operations. By outsourcing your security needs to us, you gain peace of mind, reduce costs, and free up internal resources to focus on growing your business—all while ensuring your critical data and assets remain secure.
Discover more
Threat Detection & Response (XDRaaS)
Threat Detection & Response (XDRaaS)
Protect your business with a cutting-edge service designed to detect and respond to cyber threats in real-time across your entire digital ecosystem. XDRaaS combines advanced analytics with automated responses, giving your company the ability to stay ahead of threats while minimizing disruption and safeguarding critical assets.
Discover more
SOC as a Service (SOCaaS)
SOCaaS
Streamline your security operations with a service that rapidly identifies and mitigates threats through automated workflows. AIR minimizes response times, reduces the impact of incidents, and ensures your business stays secure and operational around the clock.
Discover more
Automated Incident Response (AIR)
Automated Incident Response (AIR)
Streamline your security operations with a service that rapidly identifies and mitigates threats through automated workflows. AIR minimizes response times, reduces the impact of incidents, and ensures your business stays secure and operational around the clock.
Discover more
Vuln & Attack Surface Mgmt (VASM)
Vulnerability & Attack Surface Management
Stay ahead of cyber threats with a service that identifies vulnerabilities and reduces your exposure to risk. Vulnerability and Attack Surface Management provides continuous monitoring and actionable insights to strengthen your defenses and safeguard your critical assets.
Discover more
Cybersecurity Awareness Training
Cybersecurity Awareness Training
Empower your team to be your first line of defense with tailored cybersecurity and phishing awareness training. Equip employees with the knowledge to recognize and respond to threats, reducing risks and strengthening your organization's overall security posture.
Discover more
AI-Native Workflow Automation
AI-Native Workflow Automation
Transform your security operations with intelligent automation designed to streamline workflows and adapt to evolving threats. AI-native tools enhance efficiency, reduce manual effort, and empower your team to focus on strategic priorities while staying ahead of cyber risks.
Discover more
IT/Cybersecurity Operations
IT/Cybersecurity Operations
Optimize and secure your infrastructure with expert IT and cybersecurity operations management. Our solutions streamline processes, enhance threat detection, and ensure the resilience of your systems, so your business stays protected and operational.
Discover more
GRC as a Service (GRCaaS)
GRC as a Service
Simplify compliance and risk management with GRC as a Service, designed to align your business with regulatory requirements while mitigating risks. Our tailored approach streamlines governance, ensures accountability, and strengthens your organization's security posture.
Discover more
-
Why choose Halcyon?
-
Threat Detection & Response (XDRaaS)
-
SOC as a Service (SOCaaS)
-
Automated Incident Response (AIR)
-
Vuln & Attack Surface Mgmt (VASM)
-
Cybersecurity Awareness Training
-
AI-Native Workflow Automation
-
IT/Cybersecurity Operations
-
GRC as a Service (GRCaaS)
Why choose Us?
Our managed cybersecurity services provide proactive protection, 24/7 monitoring, and expert threat response to safeguard your operations. By outsourcing your security needs to us, you gain peace of mind, reduce costs, and free up internal resources to focus on growing your business—all while ensuring your critical data and assets remain secure.
Discover more
Threat Detection & Response (XDRaaS)
Protect your business with a cutting-edge service designed to detect and respond to cyber threats in real-time across your entire digital ecosystem. XDRaaS combines advanced analytics with automated responses, giving your company the ability to stay ahead of threats while minimizing disruption and safeguarding critical assets.
Discover more
SOCaaS
Streamline your security operations with a service that rapidly identifies and mitigates threats through automated workflows. AIR minimizes response times, reduces the impact of incidents, and ensures your business stays secure and operational around the clock.
Discover more
Automated Incident Response (AIR)
Streamline your security operations with a service that rapidly identifies and mitigates threats through automated workflows. AIR minimizes response times, reduces the impact of incidents, and ensures your business stays secure and operational around the clock.
Discover more
Vulnerability & Attack Surface Management
Stay ahead of cyber threats with a service that identifies vulnerabilities and reduces your exposure to risk. Vulnerability and Attack Surface Management provides continuous monitoring and actionable insights to strengthen your defenses and safeguard your critical assets.
Discover more
Cybersecurity Awareness Training
Empower your team to be your first line of defense with tailored cybersecurity and phishing awareness training. Equip employees with the knowledge to recognize and respond to threats, reducing risks and strengthening your organization's overall security posture.
Discover more
AI-Native Workflow Automation
Transform your security operations with intelligent automation designed to streamline workflows and adapt to evolving threats. AI-native tools enhance efficiency, reduce manual effort, and empower your team to focus on strategic priorities while staying ahead of cyber risks.
Discover more
IT/Cybersecurity Operations
Optimize and secure your infrastructure with expert IT and cybersecurity operations management. Our solutions streamline processes, enhance threat detection, and ensure the resilience of your systems, so your business stays protected and operational.
Discover more
GRC as a Service
Simplify compliance and risk management with GRC as a Service, designed to align your business with regulatory requirements while mitigating risks. Our tailored approach streamlines governance, ensures accountability, and strengthens your organization's security posture.
Discover more
The Costs of a Suffering a Cyber Attack Are Growing!
From threat detection to response, we’ve got your security covered!
Strategy
Strategy
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
vCISO Services
vCISO Services
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
IT/IS Auditing
IT/IS Auditing
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
IT/Cyber Risk Management
IT/Cyber Risk Management
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Phishing Awareness Training
Phishing Awareness Training
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
General Cyber Awareness Training
General Cyber Awareness Training
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
-
Strategy
-
vCISO Services
-
IT/IS Auditing
-
IT/Cyber Risk Management
-
Phishing Awareness Training
-
General Cyber Awareness Training
Strategy
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
vCISO Services
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
IT/IS Auditing
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
IT/Cyber Risk Management
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Phishing Awareness Training
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
General Cyber Awareness Training
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Add Your Heading Text Here
Cybersecurity complexity and workload have increased
My organization's cybersecurity team is understaffed
Regulatory compliance has become more difficult
Increase in Ransomware
Ransomware costs businesses billions annually-don't let your company be next.
Increase in Ransomware
Ransomware costs businesses billions annually-don't let your company be next.
Increase in Ransomware
Ransomware costs businesses billions annually-don't let your company be next.
Add Your Heading Text Here
Recruiting vs Staffing
Recruiting vs Staffing
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Our Boutique Approach
Our Boutique Approach
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Executive Search
Executive Search
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Recruitment Process
Recruitment Process
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Skills we seek
Skills we seek
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Placement Types
Placement Types
-Direct Hire -Part time -Full time -Contract Staffing -Direct Sourcing Channel
Discover more
-
Recruiting vs Staffing
-
Our Boutique Approach
-
Executive Search
-
Recruitment Process
-
Skills we seek
-
Placement Types
Recruiting vs Staffing
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Our Boutique Approach
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Executive Search
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Recruitment Process
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Skills we seek
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud.
Discover more
Placement Types
-Direct Hire -Part time -Full time -Contract Staffing -Direct Sourcing Channel
Discover more

The cyberthreat landscape is always evolving - so should your defenses! Partner with Halcyon Cyberworks to help protect your business from all types of digital threats, including ransomware. data breaches. phishing. hacking. scams. malware. You focus on growth, while we handle the security challenges.
Increase in Ransomware Attacks last Year
Increase in Financial Losses in 2023 ($3.94 B)
Of all Cyberthreats are Phishing or Financial Scams
Local Government
We protect local government systems and citizen data with tailored cybersecurity solutions, ensuring resilient and secure operations.

Federal Government
We deliver scalable cybersecurity for federal agencies, safeguarding classified data and critical infrastructure against advanced threats.

State Government
Our services secure state systems and networks, providing advanced threat detection and compliance to maintain uninterrupted operations.

Subscribe to our newsletter

Increase in Ransomware
Ransomware costs businesses billions annually-don't let your company be next.
Increase in Ransomware
Ransomware costs businesses billions annually-don't let your company be next.
Increase in Ransomware
Ransomware costs businesses billions annually-don't let your company be next.
Increase in Ransomware
Ransomware costs businesses billions annually-don't let your company be next.
Increase in Ransomware
Ransomware costs businesses billions annually-don't let your company be next.
Increase in Ransomware
Ransomware costs businesses billions annually-don't let your company be next.
Example Title
- Lorem ipsum dolor et sit amet
- Lorem ipsum dolor et sit amet
- Lorem ipsum dolor et sit amet
Example Title
- Lorem ipsum dolor et sit amet
- Lorem ipsum dolor et sit amet
- Lorem ipsum dolor et sit amet
Example Title
- Lorem ipsum dolor et sit amet
- Lorem ipsum dolor et sit amet
- Lorem ipsum dolor et sit amet
Example Title
- Lorem ipsum dolor et sit amet
- Lorem ipsum dolor et sit amet
- Lorem ipsum dolor et sit amet



Item Title 1
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Mauris tempus nisl vitae magna pulvinar laoreet.
Item Title 2
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Mauris tempus nisl vitae magna pulvinar laoreet.
Item Title 3
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Mauris tempus nisl vitae magna pulvinar laoreet.
Are wireless headphones really worth it?
Sit amet purus gravida quis blandit. Erat velit scelerisque in dictum non consectetur a erat nam. In metus vulputate eu scele risque felis imperdiet. Adipiscing vitae proin sagitti
Creative headphone designs
Sit amet purus gravida quis blandit. Erat velit scelerisque in dictum non consectetur a erat nam. In metus vulputate eu scele risque felis imperdiet. Adipiscing vitae proin sagitti











